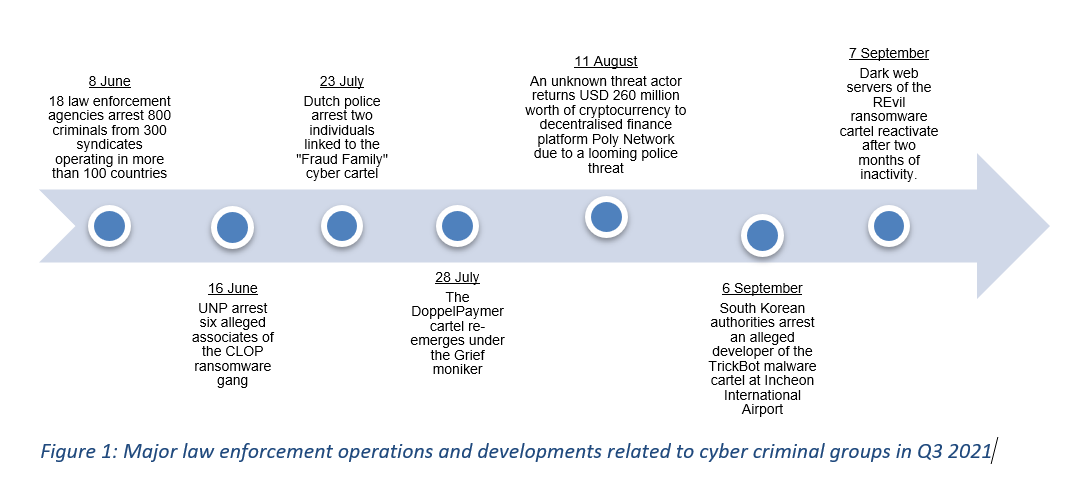
High-profile cyber groups re-emerge despite global law enforcement agencies' continued crackdown
Summary of trends:
- Q3 saw the resurgence of several cyber criminal groups previously thought to have either gone into "retirement" or in hiding due to increased clampdowns by law enforcement agencies. The most notable example is the alleged reactivation of the REvil ransomware cartel's dark web servers. This discovery follows reports that the criminal group took its various websites offline in the wake of the July 2021 ransomware attack against cloud-based management service provider (MSP) Kaseya (see Sibylline Daily Analytical Update - 14 July 2021 for more context). However, proof of the group's reactivation has emerged in recent weeks, with the ransom payment timers for all the victims targeted prior to REvil's disappearance having been reset. Moreover, the group has also begun uploading new screenshots of stolen data on its data leak site.
- Similarly, forensic investigations by cyber security researchers indicate that the new ransomware actor Grief (aka Pay or Grief) may be connected to the Russian DoppelPaymer ransomware operators. The tools, tactics, encryption file format and distribution channel (namely the Dridex botnet) are nearly identical to the ones used by the Russian criminal group. DoppelPaymer's activity has declined since the May 2021 Colonial Pipeline ransomware attack (See Sibylline Cyber Alert - 10 May 2021), precisely around the time that Grief first emerged. These similarities and the timing of its establishment increase the likelihood of the two threat actors being linked, if not the same. This would be consistent with the tactic of adopting new monikers or establishing splinter groups as a means to continue targeting industries of interest, in the face of significant pressure from law enforcement agencies.
- While law enforcement operations are likely to encourage more low-level cyber actors to shut down their activities in the coming quarter (much like Ziggy or Fonix did in early 2021), the crackdown is unlikely to significantly alter the overall ransomware threat landscape. There remains a high likelihood of other notable cyber gangs that recently went into "retirement", such as Ragnarok, using the aforementioned tactics to re-emerge in the coming months. This will sustain the ransomware threat to frequently targeted entities, such as those in government and technology.
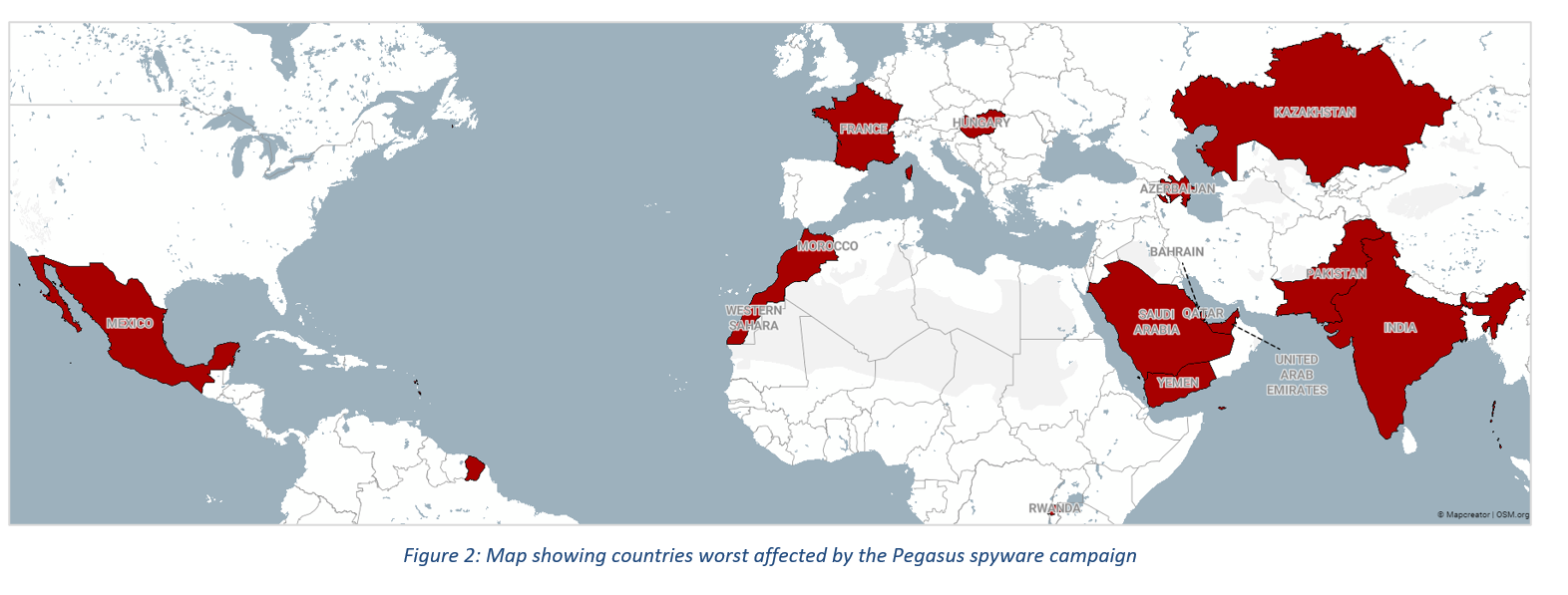
Pegasus spyware campaign will further heighten scrutiny of Israeli surveillance industry
Summary of trends:
- A consortium of international news organisations and human rights groups, including the Washington Post and Amnesty International, released a report on 18 July showing that more than 50,000 phone numbers were targeted for surveillance with Israeli surveillance firm NSO Group's spyware tool Pegasus. The phone numbers included those of opposition politicians, political dissidents, security and military operatives, independent media, students, and activists from several countries across the globe (see Figure 2). The company's policy of exclusively dealing with nation-states indicates that state-directed actors were likely responsible for these campaigns.
- This report's allegations are the latest in a series of alleged human rights violations involving NSO Group's software. It also comes almost two years after the Facebook-owned instant messaging service WhatsApp filed a lawsuit in October 2019 against the Israeli firm for helping multiple governments to monitor more than 100 journalists, human rights activists and other individuals of interest. In the wake of the Pegasus scandal, WhatsApp Chief Executive Will Cathcart suggested "numerous parallels" between the 2019 espionage activity and this most recent operation. More specifically, Cathcart noted that the targeting of these operations conflicts with NSO's software licensing agreement that its clients should only use its products to track terrorists and criminals.
- The Pegasus report is in line with a growing number of scandals involving the Israeli surveillance industry in recent years. For example, Israeli firm Toka – established by former Israeli Prime Minister Ehud Barak – has faced accusations of undermining international human rights norms by providing governments and security agencies with "spy tools for whatever device its clients require". These security firms' focus on developing bespoke cyber espionage tools has raised concern among data privacy and human rights advocates that their inability to effectively control how their clients utilise their software makes them a security liability.
- These concerns have received more attention during the Covid-19 pandemic, which has seen various governments strengthen their cyber surveillance capabilities to contain and suppress infections. The willingness of some nation states to use extra-legal measures to target not only dissident voices but also track its citizens is unlikely to diminish as the pandemic continues. Therefore, there is a high likelihood of private sector firms coming under increased regulatory scrutiny, particularly in the US and EU. This heightened scrutiny will also pose a long-term reputational risk for entities that are perceived as making use of and/or enabling these services, such as government agencies and technology firms.
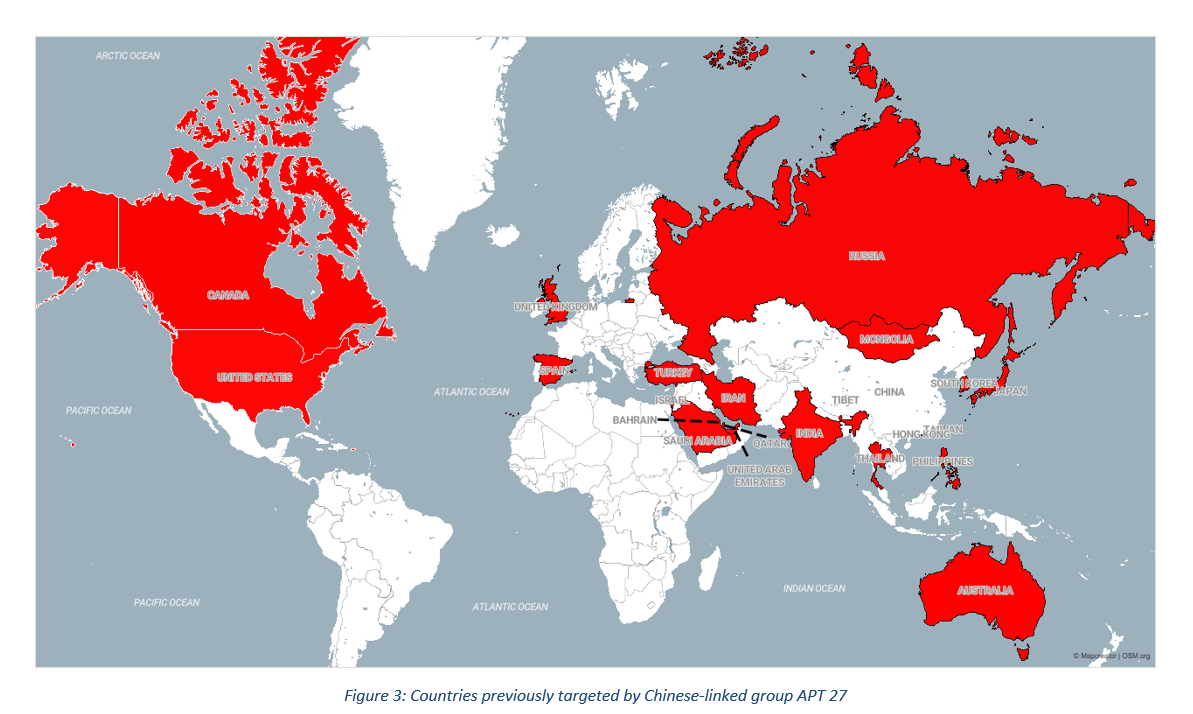
Beijing continues to utilise cyber capabilities to assess threats to business interests
Summary of trends:
- Chinese state-sponsored hacking groups continued to launch cyber espionage activity in Q3, mainly to exfiltrate intelligence on countries of strategic importance. Most notably, cyber security firm FireEye announced the discovery of a multi-year Beijing-linked espionage campaign that targeted Israeli entities across several sectors, including technology, telecommunications and defence.
- While FireEye did not reveal the Israeli entities affected, the incident underlined the Chinese government's continued use of cyber capabilities to keep track of regions where it has strategic interests. The espionage occurred against the backdrop of Beijing's growing investments in Israeli technology start-ups and partnerships/acquisitions of companies in several sectors; for example, large firms such as Alibaba, ChemChina, Huawei, and Lenovo have all either invested or made acquisitions in cloud computing, artificial intelligence (AI), semiconductors, and communications.
- The targeting of these industries also aligns with the priorities set out by China’s 14th Five-Year Plan and Vision for 2035, which aims to achieve technological superiority in several strategic industries, including AI and telecommunications. Western intelligence and law enforcement agencies – including the US Federal Bureau of Investigation, FBI) – say there is strong evidence to suggest that Beijing-linked threat actors have engaged in corporate espionage or intellectual property (IP) theft to help the Chinese government achieve these goals.
- With the aforementioned objectives set to remain at the forefront of Beijing's policy priorities in the coming years, there is an elevated risk of further Chinese-linked cyber espionage campaigns in the coming months. Entities that operate in countries that attract high levels of investment from Chinese firms, such as Israel, the Philippines or Germany, will be among the prime targets for malicious operations as Beijing attempts to secure its business interests.
Cyber criminals increasingly targeted agribusinesses in Q3
Summary of trends:
- On 1 September, the FBI Cyber Division issued a Private Industry Notification (PIN) that cyber threat actors are increasingly targeting the food and agriculture sector with ransomware-related activity. The PIN said these attacks were being used to "disrupt operations, cause financial loss, and negatively impact the food supply chain […] ransomware may impact businesses across the sector, from small farms to large producers, processors and manufacturers, and markets and restaurants". An incident involving US-based farm service provider New Cooperative exemplified this trend in late September, when the company reported suffering a "cyber security incident" that forced it to take multiple systems offline....
