Key Takeaways
RaaS will continue to grow despite sustained crackdown efforts by global law enforcement
Summary of trend:
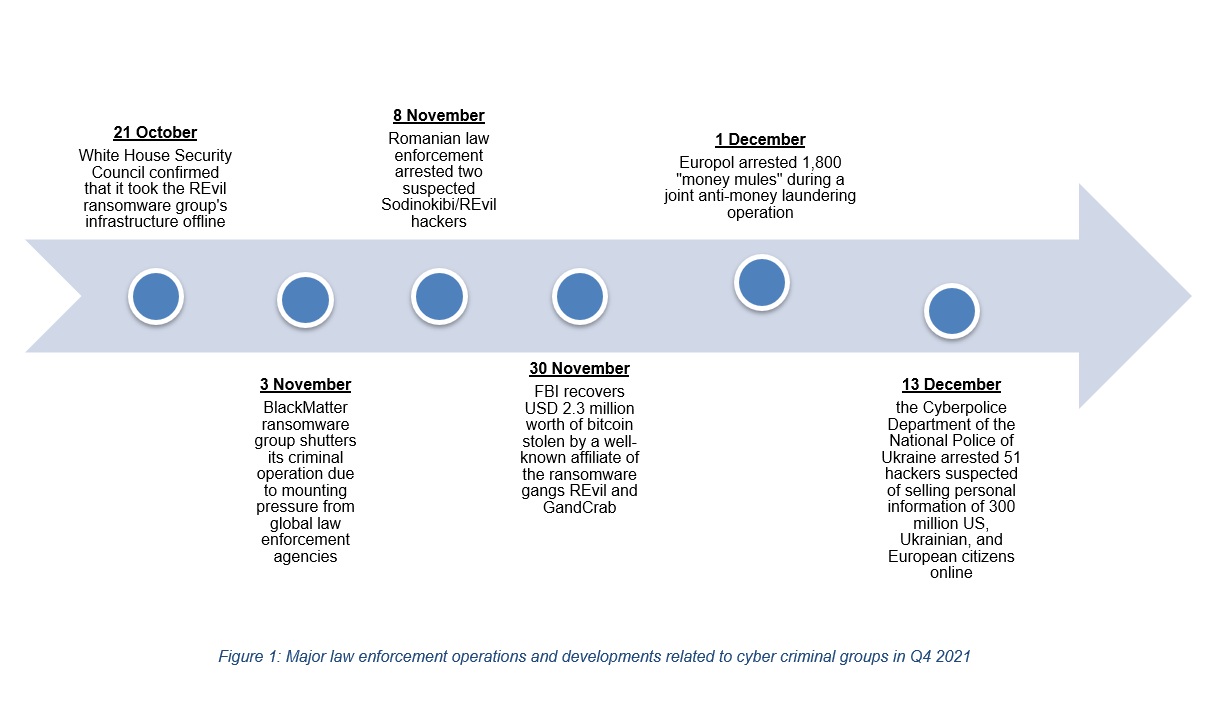
- Q4 saw global law enforcement agencies continue their crackdown on cyber criminal groups. In October 2021, the US White House Security Council announced that it shuttered the REvil ransomware group's infrastructure through a joint takedown operation. This marks the second time that the cartel's infrastructure has been taken offline since the group's operators halted their cyber activities in the wake of the July 2021 ransomware attack against cloud-based managed service provider (MSP) Kaseya (see Sibylline Cyber Alert - 6 July 2021). While REvil claimed in a dark web post following the White House Security Council-led operation that it would be permanently shutting down the cartel, this is unlikely to significantly alter the cyber threat landscape.
- Indeed, cyber criminal organisations thought to have had their operations closed down by global law enforcement agencies also re-emerged in Q4. The most notable example was the return of the notorious Emotet botnet group, which had its infrastructure seized in January 2021 during a joint law enforcement operation (see Sibylline Cyber Alert - 28 January 2021). This malware, first appeared in 2014, used infected devices to conduct spam campaigns, deliver other payloads, and/or provide ransomware threat actors with initial access to compromised systems. At the height of its operations, Emotet is believed to have infected over 1.7 million devices worldwide and caused "hundreds of millions of dollars" in damages. The group's latest activity indicates that its operators are in the process of rebuilding their botnet network.
- While it is unclear how large Emotet's infrastructure currently is, the most likely consequence of its resurgence would be the continued growth of the ransomware-as-service market (RaaS). RaaS is a highly lucrative market where ransomware operators lease out or offer subscriptions to their malware to less technical capable hackers for either a monthly fee or a cut of their ransom payments. Tracking activity at a RaaS affiliate level remains difficult. Nevertheless, high-profile RaaS operations, such as Conti or LockBit 2.0, constituted some of the most common ransomware variants used in 2021, underscoring the operational model's growing popularity amongst hackers.
- Nonetheless, global law enforcement agencies' increasing takedown operations have also had a notable impact on RaaS, with most actors adopting a "mid-game hunting" tactic to avoid attacks that would evoke a significant law enforcement response. Despite this scrutiny, RaaS will continue to grow in popularity amongst hackers due to its low technical threshold and high pay-out rates. As such, further ransomware attacks are highly likely to occur in the coming year, with small and medium-sized enterprises (SMEs) in industries such as finance, hospitality, and technology, constituting some of the most at-risk entities for this activity.
The enduring Covid-19 pandemic will remain a key factor driving malicious cyber activity
Summary of trend:
- The emergence of new, more contagious Covid variants - such as Omicron or IHU - continued to be a key factor driving malicious cyber activity in 2021. More specifically, cyber threat actors have been exploiting vaccine scepticism and pandemic fatigue to create increasingly novel pandemic-related lures to facilitate their financially motivated cyber operations. In one notable example, the Xgroup hackers published online posts in late 2021 claiming that it can, for a fee, hack into hospitals in the EU and falsify vaccination records for non-vaccinated individuals. Given the notable vaccine hesitancy and opposition to governments' implementation of restrictions or vaccine mandates in many societies, further such scams are highly likely to emerge in the coming year. The continued use of fake vaccine certificates amongst employees and customers will likely undermine companies' compliance with Covid safety protocols and increase the risk of regulatory scrutiny.
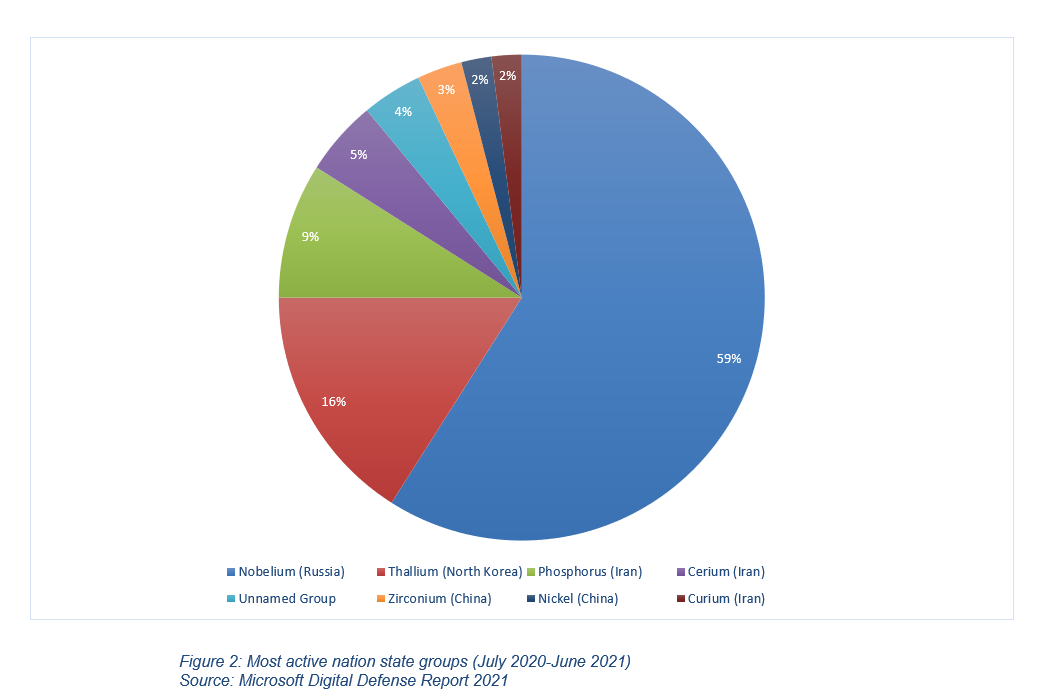
- Meanwhile, state-linked hackers have also been engaging in cyber espionage activity to acquire data related to either infection rates, country-level responses, or treatment and vaccine development efforts. For actors such as Iran, these campaigns have largely been aimed at addressing the country's shortage of well qualified and skilled labours. This "brain drain" problem has negatively impacted Iran's research and development capabilities, particularly in areas such as defence and medical science. Similar campaigns have been launched by other state actors, such as China and Russia, against medical professionals, pharmaceutical firms, healthcare institutions with the aim of helping the advance of their vaccine and treatment technology in light of the new, more infectious Covid-19 variants.
- Other state actors, such as North Korea, have utilised pandemic related lures to launch intelligence gathering campaigns aimed at fulfilling their other geopolitical goals. For example, the Pyongyang-directed Lazarus Group used Covid-themed emails to compromise organisations in the defence industry in early 2021. While the type of data targeted by these attacks is unclear, it is plausible they were designed to exfiltrate sensitive information that could help the reclusive regime further develop its ballistic and nuclear missile technology. Moreover, Beijing-linked hacking groups have utilised Covid-themed emails to help Chinese companies maintain their competitive edge in foreign markets. In October 2021, Chinese APT41 was found to be utilising Covid phishing lures to exfiltrate information on India's new income tax legislation.
With global health institutions, such as Johns Hopkins Bloomberg School of Public Health, warning that Covid-19 cases could continue to increase throughout the first half of 2022, there is a heightened risk of both state and non-state actors continuing to capitalise on companies' and individuals' pandemic-related trepidations to launch further financially motivated and intelligence gathering operations.
Social engineering will continue to grow in popularity due to low technical threshold
Summary of trend:
- The continued resurgence of Covid-19 infections has forced businesses across all sectors to further strengthen their working-from-home (WFH) capabilities to mitigate pandemic-induced shocks. As a result, hackers have increasingly adopted new tactics to target vulnerabilities in WFH arrangements. There has been a notable rise of the use of social engineering techniques. This term refers to a broad range of psychological manipulation tricks used by cyber threat actors to force their victims to give away sensitive information or make security mistakes.
- The most prominent social engineering technique used by hackers over the previous year has been business email compromise (BEC) scams. Although Nigeria is largely considered the birthplace of BEC scams, its high pay-out rates have seen cyber criminals across the globe adopting this tactic. Highlighting this trend is email security firm GreatHorn's June 2021 report, in which 35 percent of the 270 surveyed organisations claimed that "BEC/phishing attacks account for more than 50 percent of their security incidents". In line with this, such schemes have posed an increasing financial threat to businesses in recent years. The Federal Bureau of Investigation (FBI) claimed in March 2021 that nearly half of the USD 4.2 billion in cyber crime-related losses in 2020 were caused by BEC operations, romance and confidence scams, and investment fraud.
- In November 2021, the US Securities and Exchange Commission (SEC) warned that cyber criminals are increasingly targeting US investors with fraudulent schemes. These threat actors are reportedly calling, emailing, or sending letters purporting to be from SEC officials alleging they detected "unauthorised transactions or other suspicious activity" in the recipients' checking or cryptocurrency accounts, with an intent to extort money. Similar alerts have been published by other federal agencies, with the FBI warning in July 2021 that cyber criminals are impersonating registered investment professionals, such as brokers, to lure their targets into investments scams. In one notable example, a US citizen was convicted in early January 2022 for running a large-scale internet-based fraud scheme that stole an estimated USD 50 million from 70 investors between 2012 and October 2020 (see Sibylline Cyber Daily Analytical Update - 6 January 2022).
- Further social engineering-enabled attacks are highly likely throughout 2022, especially as these tactics continue to grow in popularity with cyber criminal groups due to their low technical requirements and potentially high pay-outs. High profile investors, C-Suite executives, and SMEs that publish large quantities of exploitable information online will remain the most at-risk for these scams.
Cryptojacking will re-emerge as second-tier threat amid continued teleworking arrangements
Summary of trend:
- Sibylline has observed a steady decline in cryptojacking activity since global law enforcement agencies cracked down on the popular cryptocurrency miner Coinhive in March 2019. However, the European Union Agency for Cybersecurity's (ENISA) "Threat Landscape 2021" report claimed that it detected a 117 percent increase in cryptomining malware in Q1 2021 alone. A plausible explanation for this change is cyber criminals shifting away from browser-based miners in the wake of the Coinhive crackdown and towards desktop or file-based cryptojackers. More recently, cyber criminals have been increasingly utilising the newly discovered Log4J exploit to launch cryptojacking attacks according to investigations conducted by the US Cybersecurity and Infrastructure Security Agency (CISA). It is unclear what percentage of Log4J-enable attacks are enabling this activity.
- Another notable change that has emerged in the past year has been hackers' increased targeting of organisations' cloud and container infrastructure. The Covid-19 pandemic, the subsequent surge in teleworking, has resulted in businesses from across all sectors increasing their adoption of cloud technology. Cloud-native logging and security analytics firm Devo Technology's June 2021 report found that 81 percent of surveyed organisations cited accelerating their cloud adoption timeline and plans as a result of the pandemic. While cryptojacking attacks do not inherently pose a direct threat to the data stored in cloud infrastructure, they do, nevertheless, pose a notable financial threat to businesses. Cloud providers bill their customers for consumed central processing unit (CPU) cycles. However, illicitly deployed cryptominers significant increase firms' cloud resource and electricity usage, substantially raising their overhead expenses.
- In light of this growing threat, global law enforcement agencies have stepped up crackdown against illegal cryptomining operations. For example, the Security Services of Ukraine (SBU) announced in early July 2021 that it shut down a mining operation that is estimated to have resulted in monthly electricity costs of up to USD 250,000. While these takedown campaigns will likely encourage some low-level cyber criminal organisations to close down their cryptomining operations, they are unlikely to significantly alter the overall threat landscape. Indeed, the growing proliferation of remote working technology, such as cloud computing and Remote Desktop Protocols, will likely continue to encourage more established threat actors to target industries of interest, such as technology and academic institutions.
